Table of Contents
I. Introduction: The Moment Everything Crashes
You know that feeling? The one where you’ve finished building something truly beautiful—a Laravel backend, a dynamic React front end—and watched your automated script fly into the cloud, only to crash into a brick wall? That sickening, cold realization?(Laravel Shared Hosting CI/CD Permission Fix) That is where this particular nightmare began for me. I had a gorgeous CI/CD pipeline set up with GitHub Actions, ready to conquer a standard CWP shared hosting account, only to be met by the relentless, mocking graffiti of the 403 Forbidden error.
This isn’t a bug in your code. It’s an infrastructure mismatch. Your modern Laravel application absolutely demands explicit write permissions for its cache and storage directories, a perfectly logical request that immediately hits an immovable object: the restrictive, non-root environment of shared hosting. The automation—that elegant, time-saving CI/CD pipeline that bypasses manual FTP —ironically creates the most challenging problem: the web server user suddenly can’t read or write where it needs to. Access denied. Every single time.
This guide isn’t just about the fix. It’s the entire battle plan: from the necessary application prep to the CI/CD setup, culminating in the deep dive required for the one, single, complex issue that breaks every Laravel shared hosting deployment: the Laravel Shared Hosting CI/CD Permission Fix. Get ready for command-line mastery.
II. Application Lockdown: Making Laravel Shared-Host Ready
Before you waste another moment on automation, you must, absolutely must, make sure your Laravel application is configured to survive the ancient, restrictive constraints imposed by shared hosting platforms like CWP. If you skip this, failure is a certainty.(Laravel Shared Hosting CI/CD Permission Fix)
The Migration Error that Kills Deployment
Listen, shared environments often run older MySQL or MariaDB versions, right? Or they have annoyingly conservative configuration limits. You push your migrations, and what happens? The infamous “Specified key was too long” error. Laravel’s default utf8mb4 character set is the culprit here, requiring index space that the older server configuration simply cannot accommodate.(Laravel Shared Hosting CI/CD Permission Fix)
The preemptive strike is simple: tell Laravel to play nice. You edit the AppServiceProvider.php file. You insert a single configuration adjustment inside the boot method. It looks like this:
PHP
use Illuminate\Database\Schema\Builder;
public function boot()
{
Builder::defaultStringLength(191);
}
This small, almost trivial, adjustment is essential. It ensures your automated deployments never choke on character set constraints when running database migrations.
Reconciling the Public Folder Paradox
Laravel is structured for security, keeping everything sensitive outside the document root, with /public as the sole entry point. Shared hosting, however, usually points your domain straight to /public_html. Architectural divorce!(Laravel Shared Hosting CI/CD Permission Fix)
You have two options here:
- The Pro Method: Symbolic Linking. This is the cleanest, most secure way. You keep your entire project structure intact outside the web root (e.g.,
/home/user/myproject) and create a symbolic link from the web root (/public_html) that points only to your project’s/publicfolder (myproject/public). If your host gives you minimal SSH, do this. - The Hard-Knock Hack: No symlinks? Fine. You are forced to manually move the contents of Laravel’s
/publicdirectory (including theindex.phpand.htaccess) up into/public_html. Then, you have to manually adjust the hardcoded paths insideindex.phpto locate the rest of the application outside the root. It’s clunky, but it works when absolutely necessary.
Preparing the Repository: The Exclusion Strategy
Since shared hosting environments lack the power to run Composer or npm, your GitHub Actions runner has to build the whole damn thing before it uploads the code.1 That means we have to be surgical about what we transfer via FTP.
Your .gitignore file isn’t just for Git anymore; it’s now a CI/CD exclusion manifesto. You must exclude massive dependencies (vendor, node_modules) to avoid bloat and timeouts. And, most crucially, the .env file, which contains credentials, must never be deployed. It lives securely, manually on the server.
The biggest exclusion of all? The storage/ directory. Why? If you deploy storage/ via FTP, it inherits the wrong ownership. You must exclude it to force the post-deployment, secure permission strategy that we are about to implement.(Laravel Shared Hosting CI/CD Permission Fix)
| File/Directory | Reason for Exclusion |
**/.git* | Version control metadata—pure overhead. |
**/.env | Sensitive configuration—manual placement only. |
**/node_modules/** | Front-end bloat—compiled assets only. |
**/vendor/** | Composer dependencies—massive size penalty. |
storage/ | Requires specialized, post-deployment permission handling. |
III. Building the Unstoppable CI/CD Pipeline
The solution to slow, manual FTP transfers is a workflow that runs every time you push to main. This is where GitHub Actions becomes your best friend.1
Security First: Never Hardcode Passwords
Seriously, don’t do it. We secure the FTP connection using GitHub Secrets. Go to Settings > Secrets > Actions in your repo and define these four keys:
FTP_HOSTFTP_USERNAMEFTP_PASSWORDFTP_TARGET_DIR(Don’t forget the trailing slash, or you’ll have issues 1)
Credentials are encrypted. Safe and sound.
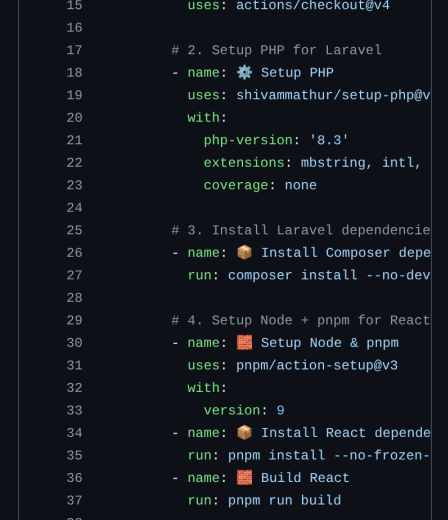
The Optimized Deployment Workflow (.yml)
We define the automation logic in .github/workflows/ftp-deploy.yml. We use the reliable SamKirkland/FTP-Deploy-Action@v4 ,.
YAML
name: 🚀 FTP Deploy Laravel App
on:
push:
branches:
- main
jobs:
ftp-deploy:
name: Deploy via FTP
runs-on: ubuntu-latest
steps:
- name: 📥 Checkout code
uses: actions/checkout@v4
- name: 🔒 FTP Deploy
uses: SamKirkland/FTP-Deploy-Action@v4.3.6
with:
server: ${{ secrets.FTP_HOST }}
username: ${{ secrets.FTP_USERNAME }}
password: ${{ secrets.FTP_PASSWORD }}
local-dir:./
server-dir: ${{ secrets.FTP_TARGET_DIR }}
exclude: |
**/.git*
**/.env
**/node_modules/**
**/vendor/**
**/tests/**
storage/
dry-run: false
That exclusion list is doing heavy lifting. It prevents unnecessary files from deploying, and crucially, sets up the storage/ directory to receive its customized, post-deployment permission treatment.
IV. The Definitive Fix: Cracking the Permission Codes(Laravel Shared Hosting CI/CD Permission Fix)
This is the ultimate moment. This is what separates a stable deployment from that infuriating 403 error.
The User Conflict: Why 755 Isn’t Enough
The root of the problem is the fight between two users:
- **The Deployer ($USER):** The FTP process, run by GitHub Actions, uploads files that are owned by your primary hosting account user ($USER) ,.
- The Web Server (
www-data): The Laravel app, when accessed by a browser, executes PHP under a low-privilege system user, typicallywww-dataorapache.
Simple, right? $USER owns the files, but www-data needs to write to them to generate logs and cache. Default 755 permissions won’t cut it, because 755 only grants R/W/X to the Owner. We need to use group permissions securely.
Command-Line Mastery: The Secure 775 Solution
We must give the web server group (www-data) write access to critical directories, while keeping everything else secure.
Step 1: Standardize Core Permissions
We ensure security across the board. Every non-critical file and folder gets standard, secure permissions.
- Files (644): Owner can Read/Write; Group/Others can only Read.
- Directories (755): Owner can R/W/X; Group/Others can R/X (Execute bit is necessary for navigation).
Run these commands at your project root:
Bash
# Set all file permissions to 644
sudo find /path/to/your/laravel/root/directory -type f -exec chmod 644 {} \;
# Set all directory permissions to 755
sudo find /path/to/your/laravel/root/directory -type d -exec chmod 755 {} \;
Step 2: The Critical 775 Fix for Writable Directories(Laravel Shared Hosting CI/CD Permission Fix)
This is the Laravel Shared Hosting CI/CD Permission Fix. The storage and bootstrap/cache directories need special handling.
First, we change the ownership group to the web server’s primary group. Assuming the server runs as www-data (verify, always! ):
Bash
# 1. Set the webserver group for the crucial directories
chgrp -R www-data storage bootstrap/cache
Second, the magic command: 775 recursively. This grants full R/W/X permissions to the Owner ($USER) and the Group (www-data). Crucially, it leaves “Others” restricted to R/X only. Security maintained. Access granted.
Bash
# 2. Grant secure R/W/X permissions to the user and the group
chmod -R 775 storage bootstrap/cache
A Note of Absolute Terror: Never Use 777
If you’re tempted to use 777, stop now. Immediately. Setting folder permissions to 777 means anyone in the world can read, write, and execute files in that directory. It’s an open invitation for hackers and malicious code. Do not do it. The 775 solution is the industry standard, secure, professional answer for shared hosting.
V. Conclusion: Launching Success
Automating a modern Laravel/React application on an ancient CWP shared server is not for the faint of heart. It requires proactive application adjustment, iron-clad security protocol, and a precise understanding of Linux file ownership dynamics.
The definitive solution—the Laravel Shared Hosting CI/CD Permission Fix—is not a single button press. It is a precise methodology: secure ownership (chgrp) followed by secure permission setting (chmod 775) on the two key writable directories. This finally bridges the operational gap between the $USER who deployed the code and the www-data user who executes it.
For final validation and stability: if you have minimal SSH access, run php artisan cache:clear immediately after deployment. If SSH is unavailable (which is likely!), manually delete the cache contents within storage/framework/cache and bootstrap/cache via your hosting file manager. Following these steps ensures your elegant CI/CD pipeline delivers a stable, functional, and securely configured application, regardless of the limitations of the shared hosting environment.
Don’t forget to check other posts –